The Multi Location Security Systems Statements
com Another peace-of-mind benefit that many individuals do not get in touch with residence protection systems is the capability for house owners to see what's going on in the home when they aren't there. Wish to check to make certain a kid got back in a timely manner from institution? Sign in through the indoor electronic cameras attached to the security system with the application on a phonesome electronic cameras are equipped with sound so parents can connect with children directly and also see that they're risk-free.
If a person has actually dropped and also is unable to reach the phone, or has actually endured a clinical emergency, that accessibility can make all the distinction in obtaining aid promptly and also using the very best opportunity for a rapid recuperation. Several residence protection business use unique packages for older relatives or those that have clinical concerns to show to their caregivers that include medical panic buttons to mobilize a rescue and the caregiver concurrently.
8 Easy Facts About Smart Home Systems Marietta Ga Shown
Finally, occasionally a package hasn't been taken, however rather misdelivered: A citizen might obtain a shipment alert with a photo of their bundle on a strange front door. Inspecting protection cameras might reveal the vehicle quiting a number of homes down the block, determining which next-door neighbor to contact for pick-up. If the burglary isn't avoided by the video camera, it may at least offer information authorities can use to connect a series of thefts to a single person and also offer evidence to the shipper or insurance coverage firm that the package was swiped, permitting some repayment.

Many checked systems include a panic button either on the system's control board, the application, or on a different vital fob to offer the consumer an easy method to summon aid fast, almost without thinking, by pushing a switch that informs the tracking service. In a dilemma, the sense you could try here that assist is on the method whether they've been able to call for it directly or not can make a big difference for a customer.
The Home Automation Marietta Ga PDFs
This info is invaluable to police as they try to locate burglars, recoup stolen belongings, and prosecute the transgressors. Additionally, the electronic cameras can basically provide an invoice for house owners insurer asserts, revealing exactly what additional hints was taken and also the problem it was in at the time of the burglary.
Why? The visibility of the systems decreases their total threat. Safety systems indicate less burglaries, which implies fewer things swiped and also less damages to repair. Monitored systems lead to much faster reactions to fires and also break-ins by fire divisions and also cops. The best security system for home protection will audibly ward off intruders as they try to barge in, protecting the residence, its materials, as well as its homeowners.
The DIY section is expected to witness the greatest development rate throughout the projection period, owing to the convenience of installment and cost-effectiveness of these systems. North America will be the leading region in the house safety and security system market share during the forecast period, owing to the enhancing fostering of residence safety systems in the area.
Multi Location Security Systems Fundamentals Explained
Many ladies are currently looking for methods to safeguard their residences as well as family members while they are away at work. Climbing disposable earnings: With a rise in non reusable revenue, even more people have the ability to pay for the expense of a house security system. This is aiding to drive the development of the market as increasingly more property owners are buying these systems - smart here are the findings home systems marietta ga.

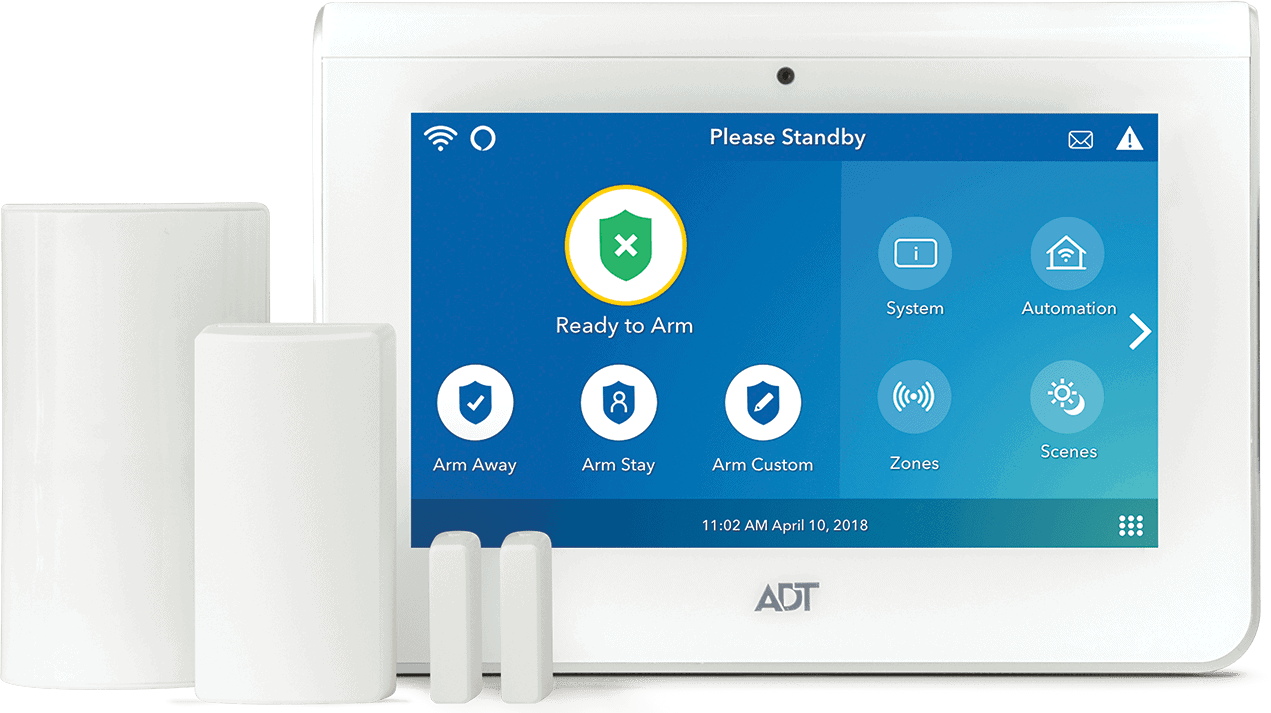
False alarm systems: House safety systems can in some cases generate duds, which can be inconvenient as well as may lead to consumers not using them. Absence of recognition: Some consumers might not be mindful of the advantages of home safety and security systems or may not comprehend just how they work, which can prevent their adoption - smart home systems marietta ga.
These areas commonly have a higher criminal offense rate as contrasted due city areas. Federal government regulations as well as plans: Federal government regulations and also plans can have a significant impact on the development of the house security system market. For instance, particular policies might call for specific kinds of systems to be set up, or limit making use of particular technologies.
Some Ideas on Home Security Companies Marietta Ga You Should Know
The USA is the biggest market among all various other areas. Europe is likewise an essential market for home safety systems, with countries such as the United Kingdom, Germany, and France driving the demand. The growing recognition of the significance of home safety and security and the raising variety of connected houses as well as the startling rates of criminal offense which have actually enhanced in the last few years.



